Types of Injection and their CHEAT SHEET
Types of Injection and their CHEAT SHEET
Xpath Injection:XPath injection is an attack targeting Web sites that create XPath queries from user-supplied data. If an application embeds unprotected data into an XPath query, the query can be altered so that it is no longer parsed in the manner originally intended. This can be done by bypassing the Web site authentication system and extracting the structure of one or more XML documents in the site.
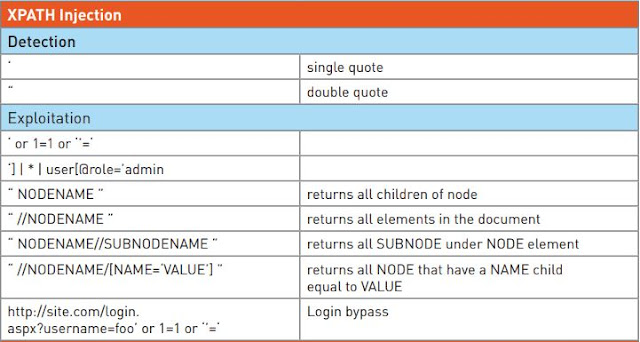
Xpath CHEAT SHEET:
LDAP Injection:
LDAP servers store information that is accessed by clients using LDAP sessions (usually with pre-defined time-outs). The most basic actions that are taken once the session is initiated are the adding, deleting and modifying of entries. Other operations that are frequently executed include:
Bind – to authenticate and specify LDAP the LDAP protocol version.
Search – to locate and retrieve LDAP directory entries.
Compare – to test if a names entry contains a given attribute value.
Extended Operation – an operation used to define unique operations.
Unbind – close the connection.
As evident in the diagram above, LDAP injections are basically crafted queries. Under normal circumstances, normal queries to the LDAP server lead to normal output. But when the malicious attacker sends LDAP statements along with code injections, additional private and sensitive information can be stolen from the LDAP servers.
Advanced LDAP injections can also allow the attacker to enable the execution of arbitrary commands to gain unauthorized permissions and even modify information within the LDAP tree. Besides these common instances, many techniques used in the SQL injection can be implemented also in the LDAP injection.
LDAP CHEAT SHEET:
Remote Code injection
Remote Code injection is the exploitation of a computer bug that is caused by processing invalid data. Injection is used by an attacker to introduce (or "inject") code into a vulnerable computer program and change the course of execution. The result of successful code injection can be disastrous, for example by allowing computer worms to propagate.
Code injection vulnerabilities (injection flaws) occur when an application sends untrusted data to an interpreter. Injection flaws are most often found in SQL, LDAP, XPath, or NoSQL queries; OS commands; XML parsers, SMTP headers, program arguments, etc. Injection flaws tend to be easier to discover when examining source code than via testing.[1] Scanners and fuzzers can help find injection flaws.[2]
Injection can result in data loss or corruption, lack of accountability, or denial of access. Injection can sometimes lead to complete host takeover.
Certain types of code injection are errors in interpretation, giving special meaning to mere user input. Similar interpretation errors exist outside the world of computer science such as the comedy routine Who's on First?. In the routine, there is a failure to distinguish proper names from regular words. Likewise, in some types of code injection, there is a failure to distinguish user input from system commands.
Code injection techniques are popular in system hacking or cracking to gain information, privilege escalation or unauthorized access to a system. Code injection can be used malevolently for many purposes, including:
Arbitrarily modify values in a database through SQL injection. The impact of this can range from website defacement to serious compromise of sensitive data.
Install malware or execute malevolent code on a server, by injecting server scripting code (such as PHP or ASP).
Privilege escalation to root permissions by exploiting Shell Injection vulnerabilities in a setuid root binary on UNIX, or Local System by exploiting a service on Windows.
Attacking web users with HTML/Script Injection (Cross-site scripting).
In 2008, 5.66% of all vulnerabilities reported that year were classified as Code Injection, the highest year on record. In 2015, this had decreased to 0.77%.[3]
Remote Code injection Cheet sheet:
XML Injection:
XML Injection is an attack technique used to manipulate or compromise the logic of an XML application or service. The injection of unintended XML content and/or structures into an XML message can alter the intend logic of the application. Further, XML injection can cause the insertion of malicious content into the resulting message/document.
XML Cheet Sheet
Os Command Injection:
These high-impact attacks basically involve the injecting of malicious commands into valid commands. Meta-characters (&, |, //;) are usually used to merge commands and create malicious OS Command Injections.
Just like SQL injections, OS Command injections can be either blind or error-based, with error-based ones being more severe due to their transparent and obvious nature.
Os Command Injection Cheet Sheet
XQuery Injection:
XQuery injection is a variant of the classic SQL injection attack against the XML XQuery Language. XQuery injection uses improperly validated data that is passed to XQuery commands. The application unsafely incorporates user data into an XQuery or XPath pattern, which can change the logic of the query.
With the XQuery injection attack, queries execute commands on behalf of the attacker that the XQuery routines have access to. XQuery injection can be used to enumerate elements on the victim's environment, inject commands to the local host, or execute queries to remote files and data sources. Like SQL injection attacks, the attacker tunnels through the application entry point to target the resource access layer.
XQuery Injection Cheet Sheet:
Server-Side Include (SSI) injection:
Server-Side Include (SSI) injection vulnerabilities arise when an application incorporates user-controllable data into response that is then parsed for Server-Side Include directives. If the data is not strictly validated, an attacker can modify or inject directives to carry out malicious actions.
SSI injection vulnerabilities can typically be exploited to inject arbitrary content, including JavaScript, into the application's response, with the same impact as cross-site scripting. Depending on the server configuration, it may also be possible to read protected files, or perform arbitrary code execution on the server, with the same impact as OS command injection.
Server-Side Include (SSI) injection cheet sheet:












In this Magch Tablet Review, we aim to determine if this tablet is the right choice for you. We will thoroughly examine its features, operating system, hardware, display unit, and battery performance.
ReplyDeleteThis article is really helpful for anyone who wants to build a career in electronics and automation! I’ve been researching training options recently and found that joining a good best embedded systems course can really strengthen both programming and hardware skills. It’s great to see how embedded systems are becoming essential in every industry. Thanks for sharing such useful insights — they’ve motivated me to learn more about this field!
ReplyDelete